Inside the word “emergency” is “emerge”; from an emergency new things come forth. The old certainties are crumbling fast, but danger and possibility are sisters.
—Rebecca Solnit, Hope in the Dark
As cases of COVID-19 continue to increase at an alarming rate, internet activity contributes its own challenges to the global crisis. The pandemic has acted as this year’s catalyst for the requisite “internet loses its mind” moment, and information security teams are under heavy pressure by a flood of new threats. Never a group to miss an opportunity to profit from uncertainty and fear, bad actors are aggressively targeting both individuals and businesses. However, the crisis has also given rise to numerous collaborative efforts and displays of altruism by registries, registrars and security professionals as they work to combat the firehose of emerging threats.
Domain registrations related to the pandemic have surpassed 100,000 since January 1, 2020. Unsurprisingly, the largest surge occurred in the week following the WHO’s declaration of COVID-19 as a pandemic on March 11, with daily registrations then doubling to more than 4,000 per day.
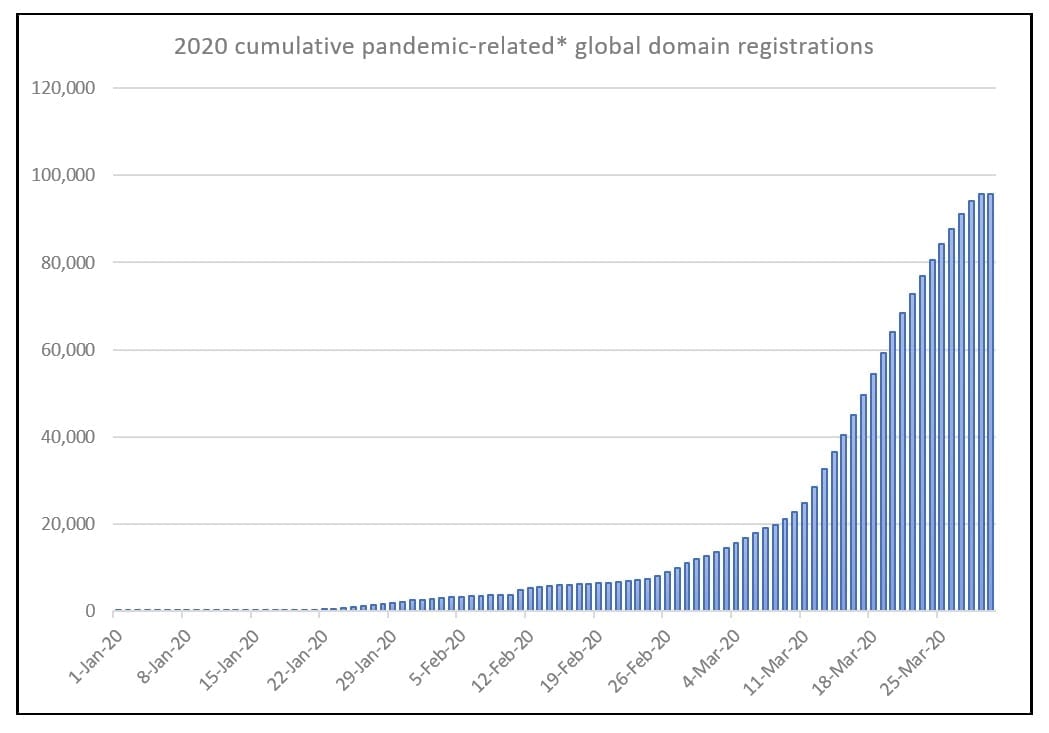
Figure 1. 2020 cumulative pandemic-related* global domain registrations. *Search terms: covid, corona, korona, kovid, pandemic, virus, wuhan. Exclusions: coronary, coronado. Source: MarkMonitor.
While the vast majority of domain registrations are speculative in nature, thousands of newly-registered domains have been identified as active threats. MarkMonitor analysts have observed three broad categories of registrations:
Government and business registrations
Governments and NGOs have leveraged pre-existing web properties such as the U.S. and European CDC sites and who.int, although some activity has been observed across third level country code top-level domains (ccTLDs), with usages mixed between redirects (e.g. covid19.gov.au) and dedicated sites (e.g. coronavirus.gov.hk). The U.S. General Services Administration put more stringent requirements in place for registration of .gov domain names in early March, four months after the previous approval process was called out by Brian Krebs, one of the world’s preeminent internet security researchers.
Business registrations have primarily occurred in the large enterprise space, with most falling into the strictly defensive category. Most identified active usages are by media organizations hosting informational sites. Our analysis identified one dedicated site, Mayer Brown’s use of covid19.law, for a dedicated legal analysis website.
Speculative registrations
Over 90% of the nearly 100,000 pandemic-related domain registrations have been registered by domain speculators looking to monetize those registrations via pay-per-click revenue or re-sale. The exact match domains aligning with the ‘coronavirus’, ‘covid19’, and ‘covid-19’ labels have all been registered across more than 400 extensions globally. Encouragingly, an assortment of registrars and aftermarket resale platforms have taken action to review recent registrations for evidence of bad actors, or even to preemptively block registrations and/or sale listings. We applaud these actions and encourage stakeholders to continue to help however they can, but should also point out that today’s parking page may be tomorrow’s malware. Threat actors understand that IT teams commonly blacklist all newly-registered domains as a best practice, and frequently allow new registrations to marinate for a time prior to turning to malicious usage.
Malicious registrations
The most concerning registrations are of course those used as an attack vector for phishing/malware threats. Lowlights include ransomware attacks on hospitals, state-sponsors phishing campaigns and attackers impersonating university health services for credential-stealing.
Registry reactions have been uneven. Nominet, the .UK registry, has escalated monitoring measures to allow quick action against inappropriate use of pandemic-related .UK domains. The step is welcomed, but absent consistent global action by registries, the ability to quickly identify threats across all top-level domains (TLD) spaces will remain spotty.
“The most concerning registrations are of course those used as an attack vector for phishing/malware threats. Lowlights include ransomware attacks on hospitals, state-sponsors phishing campaigns and attackers impersonating university health services for credential-stealing.”
With respect to registrar actions, this week the ICANN Registrar Stakeholder Group, whose membership skews to retail registrar interests, published a recommended approaches document encouraging registrars to implement heightened post-registration monitoring protocols of pandemic-related domains.
Concerned groups recently came together to form the COVID19 Cyber Threat Coalition Slack channel, which can be joined here. This channel features a wealth of information and links to additional resources, and we encourage MarkMonitor clients to join in order to keep tabs on current and emerging threats. As of writing, more than 2,100 vetted domain/subdomain threats have been discovered and catalogued here. These vetted threat lists are living documents categorized by IP address, hash and URL, and are currently the most easily-ingested source of blacklists for security teams. For security researchers interested in threat details, AlienVault is cataloguing threat details via a free resource here. DomainTools is also providing a raw free COVID-19 Threat List, updated daily.
Recommended actions
MarkMonitor encourages those with the knowledge and/or resources to benefit cooperative initiatives to contribute in whatever manner possible. Internally, a few simple actions will help your organization to reduce risk:
- Defensive registrations: While many organizations will not be targeted by bad actors, those that fall into the generally high-risk target group should consider at least a few defensive registrations, e.g. companynamecovid-19.com, companynamecoronavirus.com.
- Registry-lock of mission-critical domain names: Failure to registry lock business-critical domains (which takes approval for critical infrastructure actions like DNS record changes offline) is an invitation to threat actors. The cost/benefit favors registry lock on orders of magnitude. Just this week, another “why wasn’t that domain registry-locked?” issue occurred at GoDaddy involving escrow.com, a platform used to transact hundreds of millions of dollars in secured transactions involving everything from cars to—ironically—domain names.
- Email validation: SPF, DKIM, and DMARC records are designed to combat email spoofing, and are a fundamental best practices step that should already be in place on all domains receiving email. A quick check to confirm is well worth the time, if your company’s implementation status is unknown.
Stay safe, everyone. Continue checking our blog posts for additional updates related to COVID-19, or access the Clarivate complimentary resource site here.





